Network Programming & Tricks

Network programming is the use of computer codes to write a program that can communicate with another program through a network. In this post, I'll examine network programming and the technologies used in this important field to the applications of network programming. An area where developers take help from various programming languages, libraries and protocols to implement and run it.
A network is a set of devices connected to each other to exchange information such as email, documents, audio and video files or share resources between physical devices such as printers and storage spaces. The computers in each network are called "Host" and the components connecting them to each other are called "Links". In the list below, you can see some examples of the network:
- Establishing a connection between a printer and a computer.
- Send files from one device to another using Bluetooth.
- Communication between browser software and website hosting servers or viewable and downloadable files.
The above are just a few examples of the network that were mentioned for more familiarity and better understanding of the subject.
Computer networks have different types and are divided into the following categories based on size:
- Local Area Network (LAN): It is the connection of a small number of hosts or computers in a limited space. All networks used in homes, schools and offices are of this type.
- Metropolitan Area Network (MAN): A larger network than a LAN that covers the entire urban area and is conceptually equal to several LANs connected to each other.
- Wide Area Network (WAN): A collection of smaller networks such as LANs and MANs that are interconnected and have global coverage. In fact, the Internet is the largest WAN network.
- Wireless Local Area Network (WLAN): A type of communication system that uses radio frequencies to transmit and receive information, reducing the need for legacy connections.
- Virtual Private Network (VPN): The encrypted internet connection between user devices and the network is called VPN. With the help of VPN, you can ensure the safe transfer of data and prevent unauthorized access to the network.
- Storage Area Network (SAN): A high-speed network that provides server access to storage devices by integrating the storage space and the operating system. In this way, it becomes easier to manage and access the storage space.
"Socket programming" is one of the most important aspects of network programming. Sockets are the communication endpoint between two applications on the network and allow processes to send and receive data over the network. In fact, socket programming is the foundation of many networking applications that we use every day. From web browsers to messaging apps and online games. In fact, socket programming is one of the main techniques used in network programming. When you're programming for a network, you often rely on sockets to communicate between clients and servers, send and receive data, and manage network connections.
Among the various programming languages, Python is one of the best options for socket programming. Python has suitable libraries for working with sockets, which makes their use very simple and effective.
Common terms in the network
Network terms may seem confusing at first. Especially for people who have just started their activity in this field.
- Network: A set of connected devices such as computers, printers, and servers that are connected to each other.
- Node: Any device connected to a network, such as a computer, printer, or router, has the role of a node.
- Protocol: A set of principles and rules that determine how to communicate between devices in a network.
- IP Address: A sequence of unique numbers assigned to devices on the network and used to identify and communicate with other devices.
- Router: A device that connects several different networks and transfers information packets between them.
- Switch: A device that connects several devices in a network and transfers data packets from one device to another.
- Domain Name System (DNS): A system that translates Internet domain names into equivalent IP addresses and enables devices to identify and connect to websites and other network resources.
- Dynamic Host Configuration Protocol (DHCP): A rule or protocol that automatically assumes appropriate IP addresses and settings for network devices.
- TCP/IP protocol: A set of protocols used to communicate between the Internet and other networks.
These terms are just a few of the basic network concepts that are necessary and important to understand in order to learn more complex topics.
What is network programming?
Computer networks can be examined at two levels of hardware and software. Each network consists of a number of computers, cables and other tools required for setup. Understanding computer networks at the hardware level requires familiarity with various sciences such as physics, mathematics, and electronics, and we must also be familiar with the basic technologies and components of computers. On the other hand, the software layer consists of programs, instructions and algorithms that make the hardware part work.

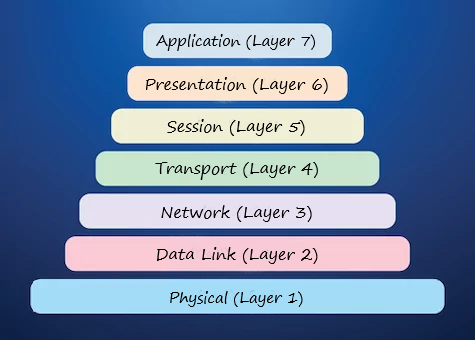
Network programming is the development of programs that can communicate with other programs through a computer network. For example, the HTTP protocol describes how to receive and share resources such as text documents over a network. It also provides users with a detailed description of the hardware components required for resource exchange. Although the list of existing network protocols is extensive and scattered across different fields, they all follow a model known as Open Systems Interconnection (OSI).
The OSI model serves as a guide for network professionals, developers, and other people involved in network programming and helps them gain a proper understanding of how products and software communicate and interact. This conceptual framework provides an overview of how computer networks work. A model with seven layers that describes how data flows along the network. In the picture below, the general outline of the OSI model with seven layers "Physical", "Data Link", "Network", "Transport", "Session", "Display" "Presentation" and "Application" are drawn:
The hardware of a network-related device is closely related to the operating system and other software and forms a closed and interdependent system. As a result, the innovation and development of one sector requires mutual updating of another sector. Through network programming, the solution of the desired problem can be summarized in a set of understandable and executable instructions for the computer.
According to today's standard hardware, software-defined functions and open-source models, Professor Nick McKeown's research team proposed a new network architecture called Software-defined Networking (SDN), which not only It can be implemented and run on computers as well as other related hardware. In SDN architecture, the network control unit is separated from the information unit. It is worth noting that over the years, the development and generalization of the information or data unit, similar to the common hardware of computer systems, has increased.
It is no longer necessary to set up the computing unit separately for different network protocols and instead only the commands received from the control unit are executed. Defining the computing unit and the logic of network devices is the responsibility of the software compatible with the SDN architecture.
Network programming is the main characteristic of SDN architecture. In fact, this architecture provides access to a variety of APIs for network configuration and management.
OpenFlow
A protocol that can be used between the control unit and the information architecture of SDN, which was introduced in 2008 by Professor Nick McQueen and his colleagues. The design principles of OpenFlow are such that the two processes "Matching" and "Action" play the role of the main operations, and the "Controller" section is used to transfer the "Flow Table" records to the "Switch" device. . In the OpenFlow protocol and for information exchange, a unique communication path or so-called channel is established between the switch and the controller. During this process, it is possible to send "Pockets" to the user interface or ignore them by protocols such as "Ethernet", IPv4 and IPv6.
The task of programming the network in OpenFlow is the responsibility of the controller part. For example, first one of the houses of the flow table is sent to switch A, and from that side a packet is transferred to the IP address 192.168.1.20. In short, OpenFlow is a kind of SDN-related technology that extends some principles and rules of network processing and also supports "centralized programming".
POF
Similar to OpenFlow, POF architecture also consists of two parts: control unit and information unit. An architecture that summarizes the network processing process into more interactive parts while supporting the sending rules and logic.
P4
Among the advantages of P4 over OpenFlow, it can be mentioned that it is easier to program. The P4 architecture processes and manages packets by defining a program that includes Header, Parser, Table, Action and control program. Among other advantages of this architecture, we can refer to redefining network settings without disrupting the process of sending packets.
Among the most common applications of network programming, we can mention "Data Transfer". A process that involves sending and receiving information between two or more devices. For example, when you visit a website, the browser sends a request to the web server and returns the desired page as a response. In data transfer, according to the type and format of the information as well as the network architecture, various protocols such as HTTP, FTP, SMTP and TCP/IP are used. In addition, in data transmission, it is also possible to use encryption and compression techniques.
Remote access allows users to remotely access and manage a device or system. For example, when using software like TeamViewer, you can control a computer in another location. In general, "Remote Access" depends on the level of security and performance and is done with protocols such as SSH, RDP, VNC and Telnet. Also, in the application of remote access, it is possible to use authentication mechanisms to confirm the access of users.
Another important application of network programming with the ability to provide information for external services is web services. For example, weather software uses Web Services to receive information such as temperature and weather forecast. Web services format based on network interface and data structure can be one of XML, JSON, SOAP and REST.
Network programming allows users to compete with each other in a virtual, networked environment. Like when you join a server in an online game and compete against other players from all over the world. In online games, depending on the type of scalability and network stability, different structures such as "Client-Server", "Peer-to-Peer" or "Hybrid" can be used.
Distributed computing is the use of multiple devices or systems to perform complex calculations or processes over a network. For example, when you use a cloud computing service, you will have access to the resources and power of several servers. "Parallel", "Grid" and "Cluster" models are the most used in distributed computing.
Network security is one of the important topics in network programming, which should be given special attention in all the mentioned applications. With the spread of cyber threats, protecting data and network infrastructure has become an undeniable necessity. Network developers should always include security principles in the design and implementation of their programs to avoid possible vulnerabilities. There are several solutions to protect computer networks from intrusion and hacking. Using strong encryption to protect data in transit, implementing authentication systems, regularly updating software and operating systems, using firewalls and intrusion detection systems all play a significant role in securing the network.

Congratulations!
✅ Good job. Your post has been appreciated and has received support from CHESS BROTHERS ♔ 💪
♟ We invite you to use our hashtag #chessbrothers and learn more about us.
♟♟ You can also reach us on our Discord server and promote your posts there.
♟♟♟ Consider joining our curation trail so we work as a team and you get rewards automatically.
♞♟ Check out our @chessbrotherspro account to learn about the curation process carried out daily by our team.
🏅 If you want to earn profits with your HP delegation and support our project, we invite you to join the Master Investor plan. Here you can learn how to do it.
Kindly
The CHESS BROTHERS team
Hello,
this Comment has been upvoted with 47.8%, thanks to @albro who burned 478 PLANET
With this burn @albro is actively participating in the CLEAN PLANET reward protocol.
@albro is helping @cleanplanet to grow with the curation.
Thanks for your help
@cleanplanet